The Edgescan Platform
Enterprise-scale vulnerability detection.
Guaranteed, validated accuracy.
Full-stack security coverage.
The 2024 Vulnerability Statistic Report
is now available!

Visit with us March 19, Cyber Europe, LondonMarch 20, Cybersecurity Summit, RosemontMarch 23, Zerodays, Dublin to learn more about Edgescan
One platform. Complete visibility. Fixed costs.
External Attack Surface Management
(EASM)
Risk-based Vulnerability Management (RBVM)
Prioritized remediation.
Application Security Testing (AST)
Risk-rated results.
API Security
Testing
Immediate Risk Triage.
Penetration Testing
as a Service
(PTaaS)
+ Analytics + Automation
Free Training Courses: Master the Fundamentals of Secure Coding
Offered in partnership with Manicode Security

Edgescan was listed as one of the “notable vendors” for EASM in the Q1 2023 Forrester Landscape for External Attack Surface Management
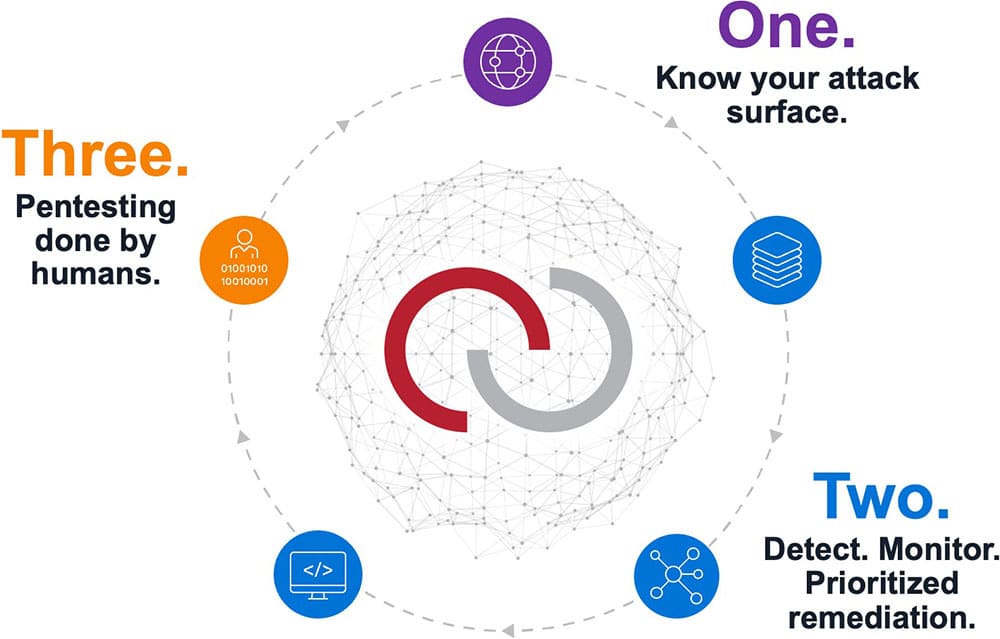
Learn about our three-step approach to securing your attack surface.
An excellent solution when it comes to vulnerability assessment and management.
Fantastic product and support!Should have used it sooner.
Award-winning products. Amazing people.

What our customers think...
"The accuracy that comes with human validation, paired with the efficiency of automatic and continuous scanning, means that my team now knows that whenever a vulnerability is flagged, the vulnerability is there, and they can continue working until they find it and fix it."

I have been extremely impressed with EdgeScan from Sales to Operations. Furthermore, I have had nothing but positive experiences. Just to say thank you to the full team for all their challenging work in 2022 and look forward to continuing our relationship in 2023.”

The system is very efficient and reliable. Always works as advertised. The functionality to track issues is extremely useful.

I have been an Edgescan customer for over five years and continue to be impressed by the Edgescan team hitting all the notes so well: innovation, quality, integration, scale, cost customer support, responsiveness, and true partnership.


